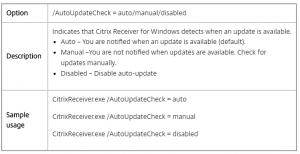
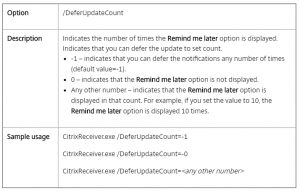
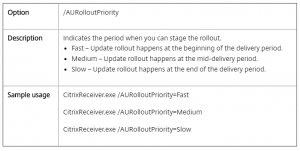
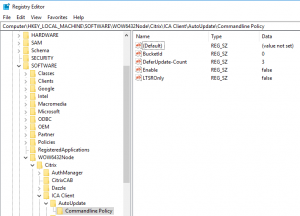
If you have, many websites Load Balancing on the NetScaler you properly use Content Switching to minimize the need of IP addresses. For this to work you have policies and actions to control the traffic flow. However, do you know that with NetScaler you can use expressions to configure the Content Switching actions?
This can come in handy when managing multiple websites Load Balancing. Let me show you a short configuration to demonstrate how this I working.
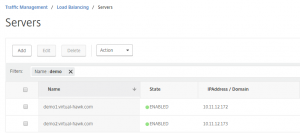
I have 2 demo web sites configured demo1.virtual-hawk.com and demo2.virtual-hawk.com. I have created the servers with FQDN names, as I am using host names on the web sites.
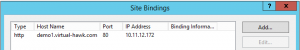
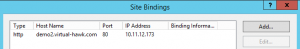
IIS configuration:
NetScaler Server configuration:
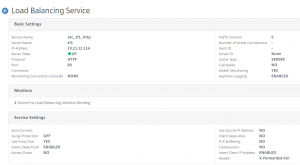
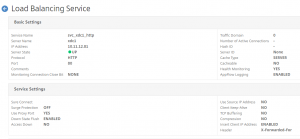
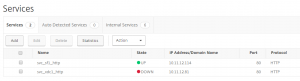
I then created 2 service for the web sites:
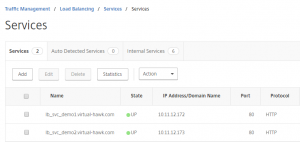
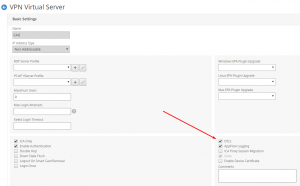
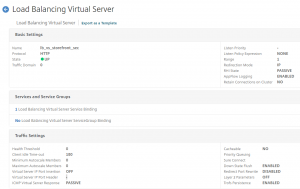
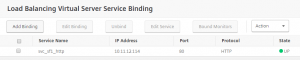
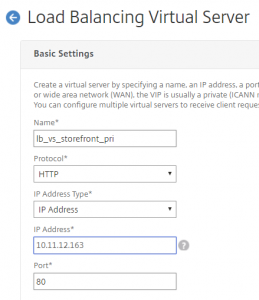
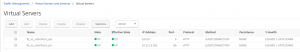
2 Load Balancing Virtual Serves for the Content Switching to go to. These are “non addressable”, because all traffic will come through the Content Switching Virtual Server:
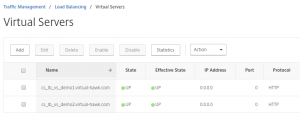
The important thing is the naming of the Load Balancing Virtual Server, as we will use that in the Content Switching Action.
I have made a Content Switching Action with expressions used for targeting the Load Balancing Virtual Server:
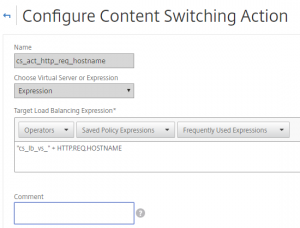
With the use of the expression “cs_lb_vs_” + HTTP.REQ.HOSTNAME, the action will go to cs_lb_vs_demo1.virtual-hawk.com if the client request the site demo1.virtual-hawk.com.
The Content Switching Policy, I only need 1:
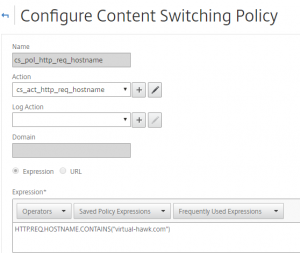
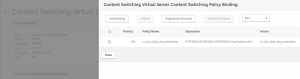
Finely I created the Content Switching Virtual Sever, and bound the policy to it:
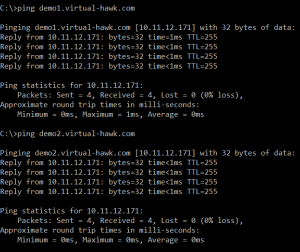
Now for the test I checked the demo1.virtual-hawk.com and demo2.virtual-hawk.com are going to the Content Switching Virtual Server on 10.11.12.171:
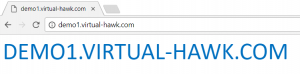
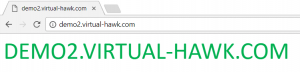
When I test from the browser, I get the flowing:
Conclution:
With the use of Content Switching Action expressions, we can minimize the NetScaler configuration. For any new sites, I only have to configure the Load Balancing Virtual Servers with the right naming and no more. All the Content Switching are still the same and already configured.
CLI Commands:
add server demo1.virtual-hawk.com 10.11.12.172
add server demo2.virtual-hawk.com 10.11.12.173
add service lb_svc_demo1.virtual-hawk.com demo1.virtual-hawk.com HTTP 80 -gslb NONE -maxClient 0 -maxReq 0 -cip DISABLED -usip NO -useproxyport YES -sp OFF -cltTimeout 180 -svrTimeout 360 -CKA NO -TCPB NO -CMP NO
add service lb_svc_demo2.virtual-hawk.com demo2.virtual-hawk.com HTTP 80 -gslb NONE -maxClient 0 -maxReq 0 -cip DISABLED -usip NO -useproxyport YES -sp OFF -cltTimeout 180 -svrTimeout 360 -CKA NO -TCPB NO -CMP NO
add lb vserver cs_lb_vs_demo1.virtual-hawk.com HTTP 0.0.0.0 0 -persistenceType NONE -cltTimeout 180
add lb vserver cs_lb_vs_demo2.virtual-hawk.com HTTP 0.0.0.0 0 -persistenceType NONE -cltTimeout 180
bind lb vserver cs_lb_vs_demo1.virtual-hawk.com lb_svc_demo1.virtual-hawk.com
bind lb vserver cs_lb_vs_demo2.virtual-hawk.com lb_svc_demo2.virtual-hawk.com
add cs action cs_act_http_req_hostname -targetVserverExpr “\”cs_lb_vs_\” + HTTP.REQ.HOSTNAME”
add cs policy cs_pol_http_req_hostname -rule “HTTP.REQ.HOSTNAME.CONTAINS(\”virtual-hawk.com\”)” -action cs_act_http_req_hostname
add cs vserver cs_vs_virtual-hawk.com HTTP 10.11.12.171 80 -cltTimeout 180
bind cs vserver cs_vs_virtual-hawk.com -policyName cs_pol_http_req_hostname -priority 100