This week with a Citrix Storefront upgrades a ran into an error, when joining a Citrix Storefront Server to a Storefront Server Group.
In the upgrade i follow this process:
• Disable Server A in the Citrix NetScaler configuration
• Remove Server A from the Citrix Storefront Group
• Reboot Server A
• Upgrade Citrix Storefront on Server A
• Enable Server A in the Citrix NetScaler configuration
• Disable Serve B in the Citrix NetScaler configuration
• Uninstall Citrix Storefront
• Install Citrix Storefront new version
• Join Citrix Storefront Server Group
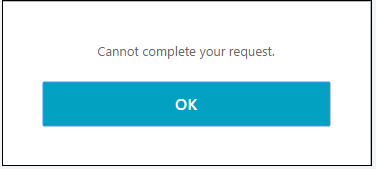
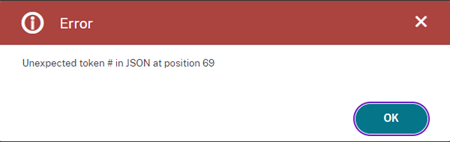
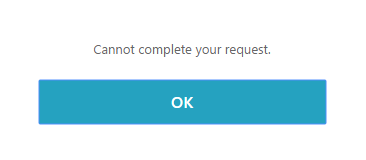
When doing the Join Citrix Storefront Server Group a got this error:
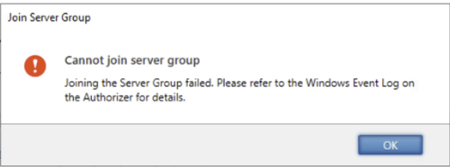
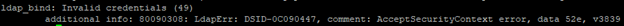
When examining the Windows Event log I found this error:
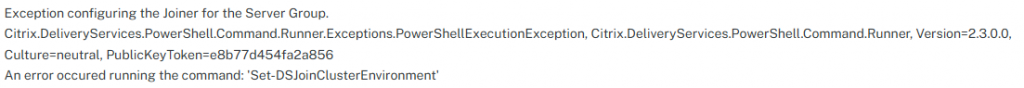
That did’t help me, as this do not explain what was going on.
After some trial an error, a finely found this in the Citrix Storefront log files (C:\Program Files\Citrix\Receiver StoreFront\Admin\logs)
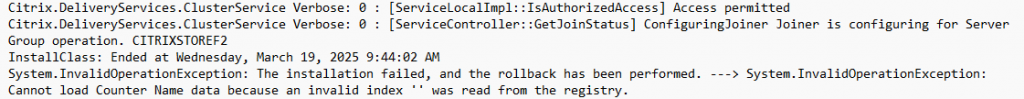
After searching for the “Cannot load Counter….” I got a hit on rebuilding the Performance Monitors whit the commando “lodctr /r” in a admin command prompt.
After the rebuild of the Performance Monitors there was no problem joining the Citrix Storefront Server Group.